August 25th, 2021 by Admin
There’s no doubt that enterprises today, more than ever, need effective cybersecurity strategies. However a sound strategy is not in and of itself a guarantee of success. There are several ingredients that are necessary for a cybersecurity program to be successful. This chapter will describe what a cybersecurity strategy looks like and each of the necessary ingredients for success in detail.
August 25th, 2021 by Admin
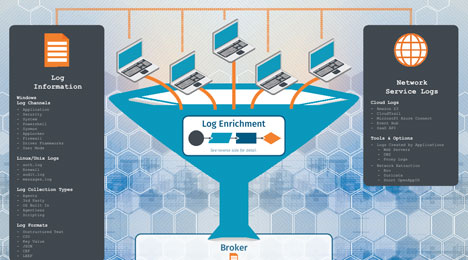
Security operations aren’t suffering from a “big data” problem – but rather a “data analysis” problem. A SIEM can be an incredibly valuable tool for the SOC when implemented correctly. Leverage the Log Lifecycle Poster to add context and enrich data to achieve actionable intelligence – enabling detection techniques that do not exist in your environment today.
August 25th, 2021 by Admin
This SSH Cheat Sheet contains SSH commands you need for your daily linux administration. SSH which is also referred to as Secure Shell is a cryptographic network protocol for operating network services securely over an unsecured network. To start using different ssh command-line options, follow this guide and practice in Virtual environments.
August 25th, 2021 by Admin
MySQL is a popular, open-source, relational database that you can use to build all sorts of web databases — from simple ones, cataloging some basic information like book recommendations to more complex data warehouses, hosting hundreds of thousands of records. Ready to advance your coding skills and master databases? Great! Then you will find our MySQL cheat sheet absolutely handy.
August 24th, 2021 by Admin
In 2019, 12,174 new vulnerabilities were found in commercial and open source software1. The total number of breached records were 15.1 billion. This is a 284% spike compared to 2018.
Categories
Disclaimer
Unless otherwise indicated, Copyrights and Intellectual Property Rights of the documents, reports in this section of the website are under ownership of the original authors. Readers and Users of the information in the form of documents, reports and requested to comply with More..